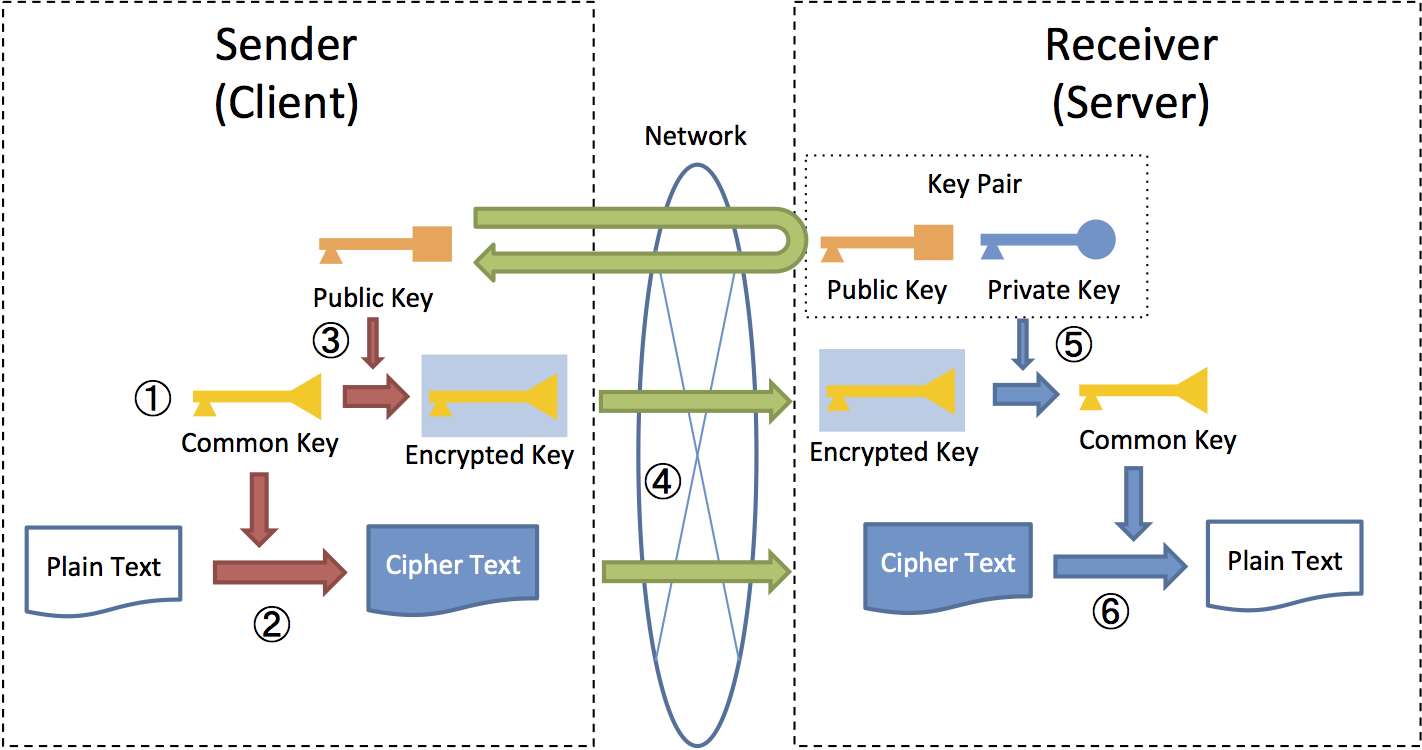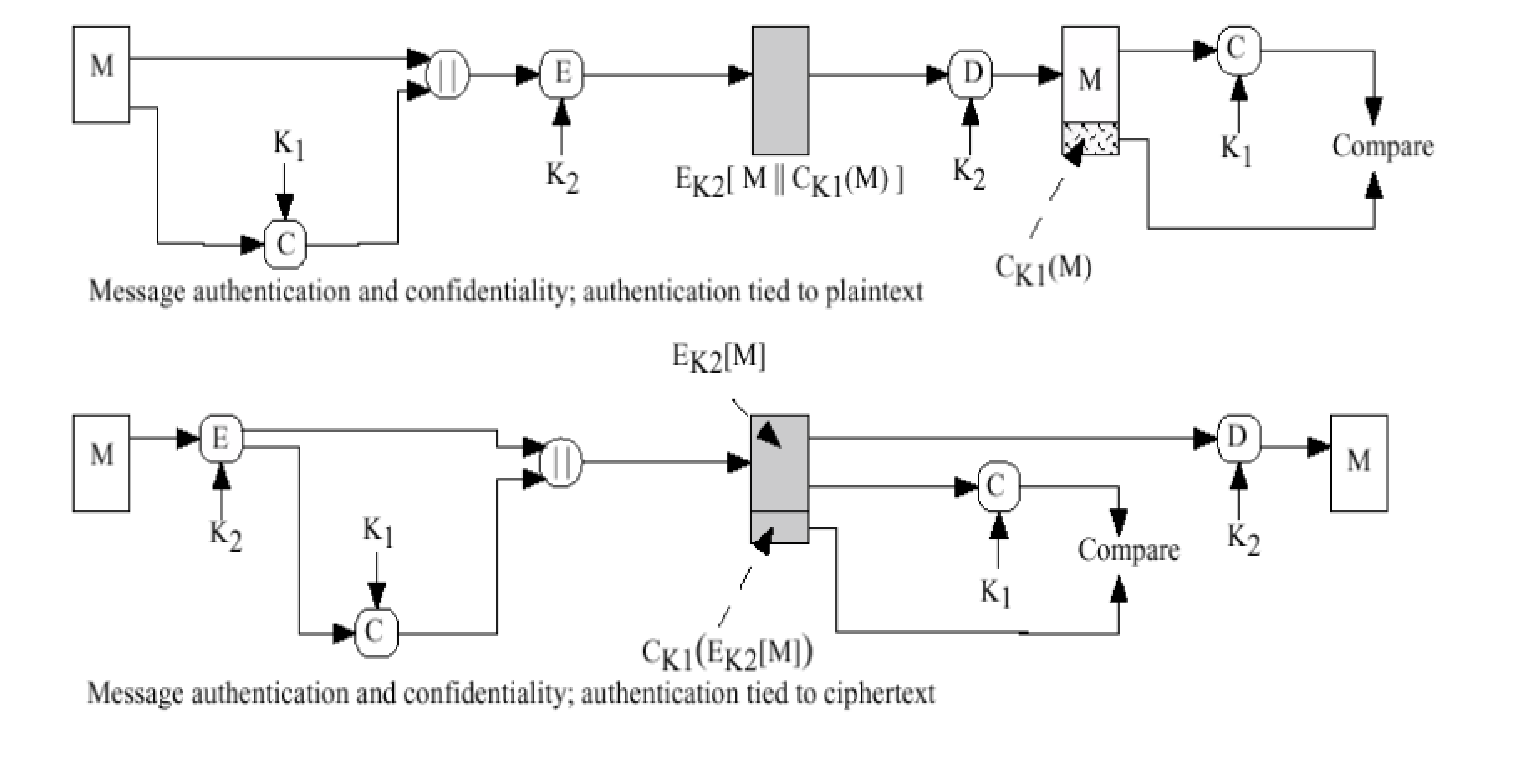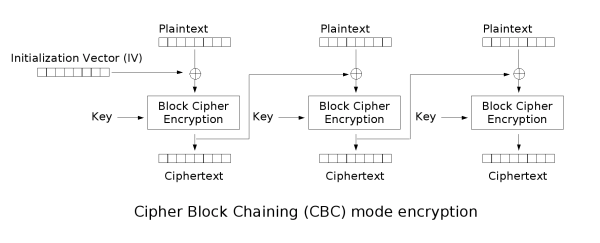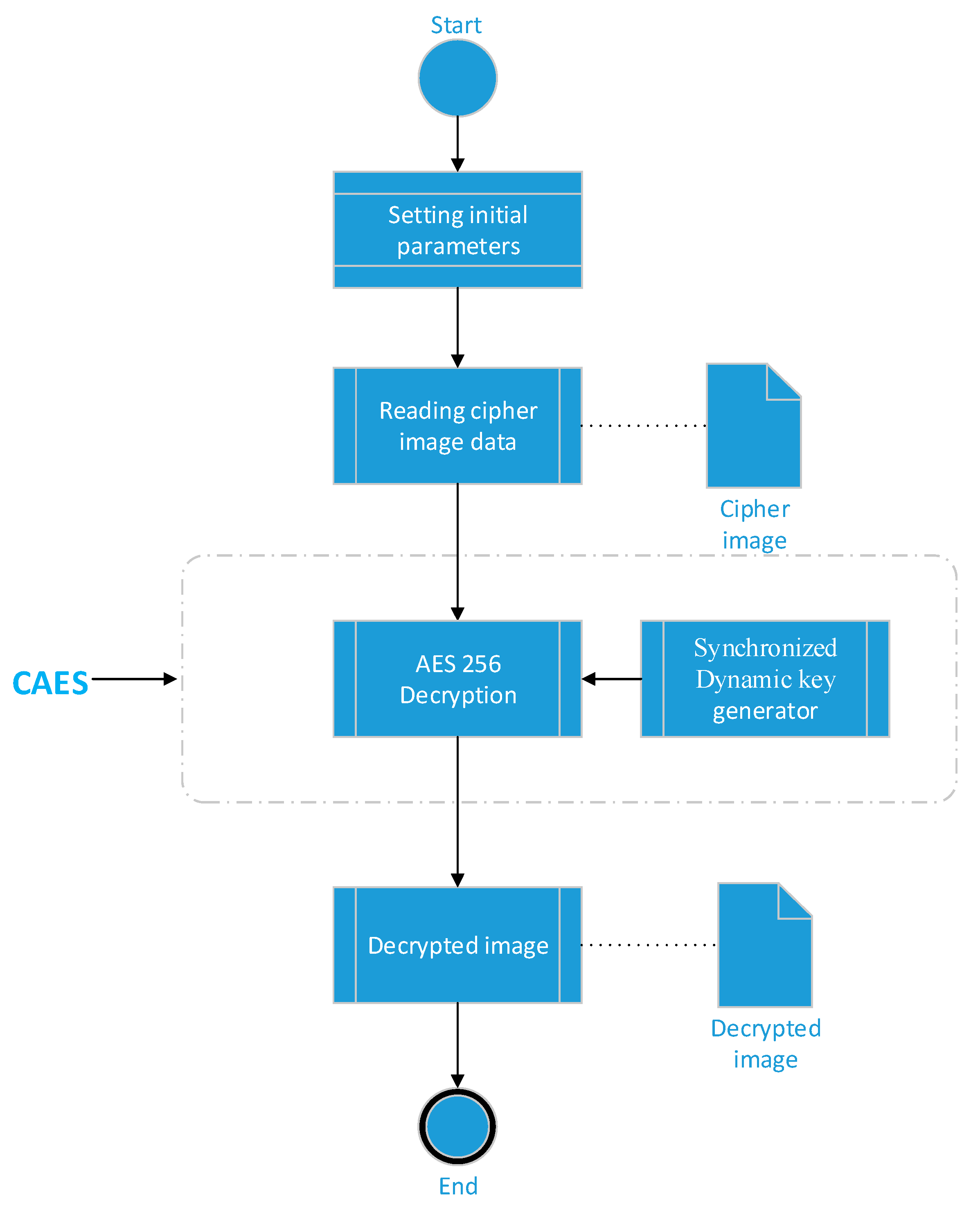
Applied Sciences | Free Full-Text | Chaos-Based Synchronized Dynamic Keys and Their Application to Image Encryption with an Improved AES Algorithm
Security Best Practices: Symmetric Encryption with AES in Java and Android | by Patrick Favre-Bulle | ProAndroidDev

A Comparison of Cryptographic Algorithms: DES, 3DES, AES, RSA and Blowfish for Guessing Attacks Prevention