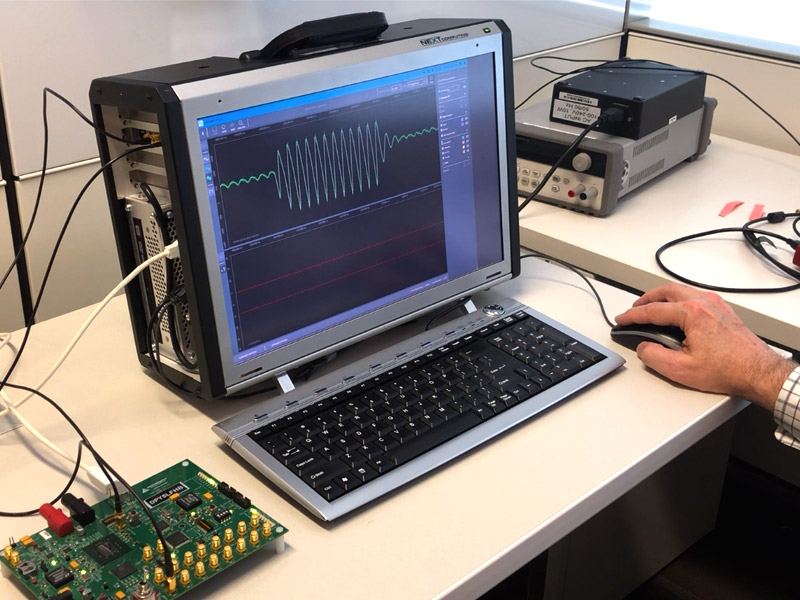
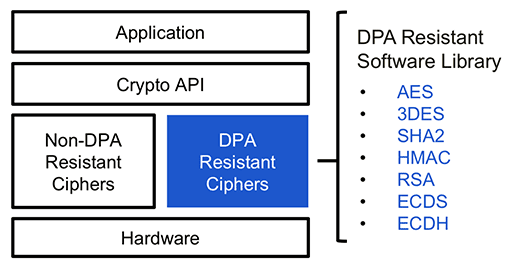
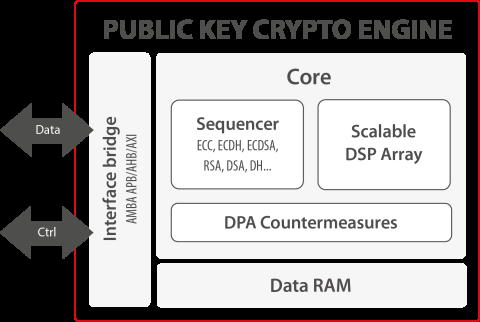
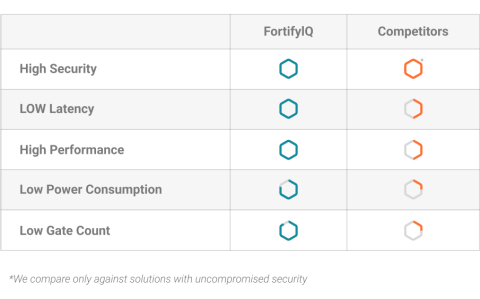
Figure 1 from Side-channel attack resistant AES cryptographic circuits with ROM reducing address-dependent EM leaks | Semantic Scholar
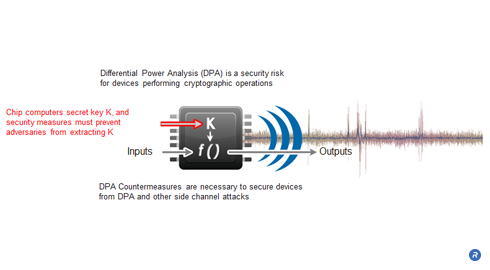
Cryptography | Free Full-Text | Power Side-Channel Attack Analysis: A Review of 20 Years of Study for the Layman

Guarding Machine Learning Hardware Against Physical Side-channel Attacks | ACM Journal on Emerging Technologies in Computing Systems
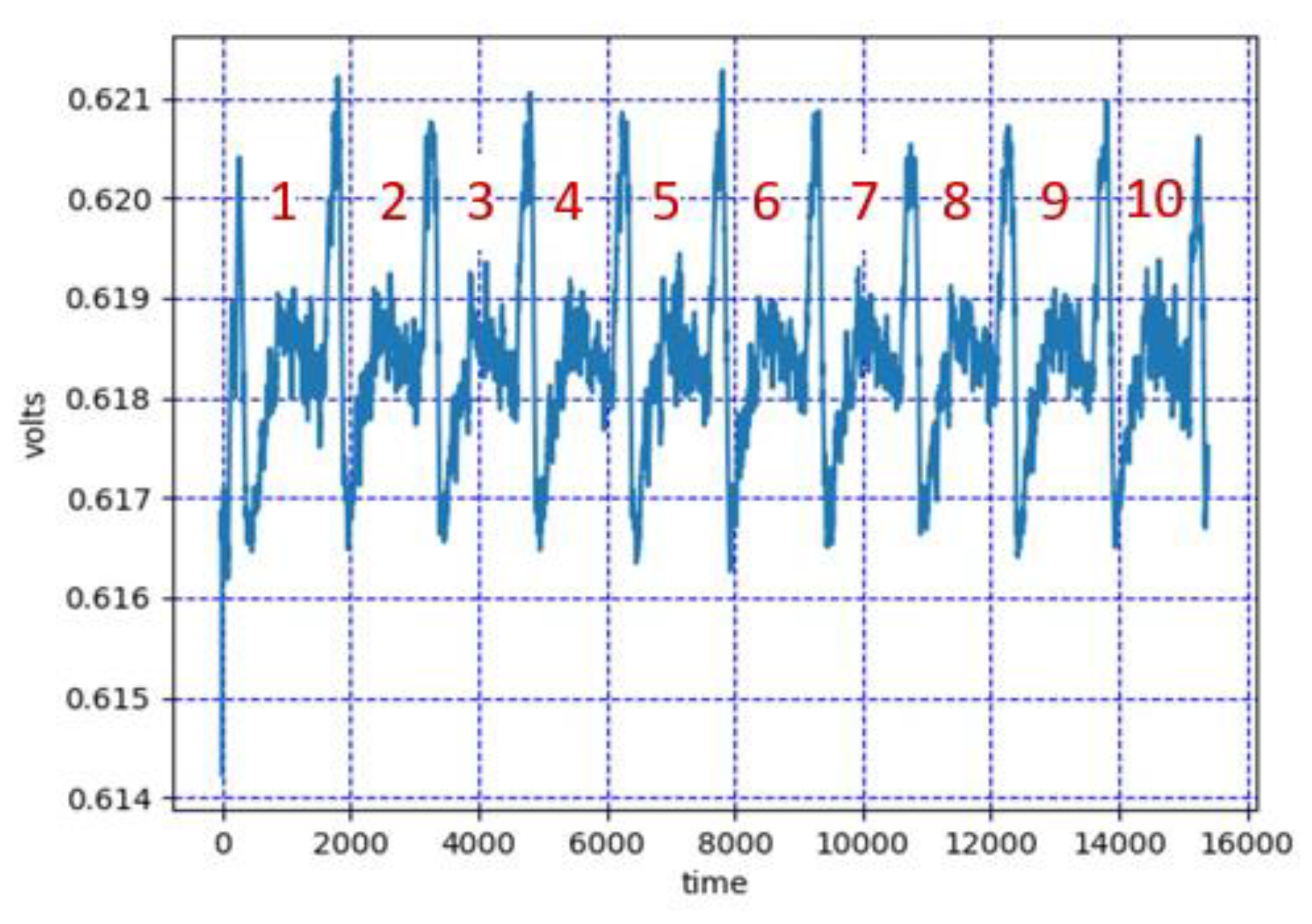
Cryptography | Free Full-Text | Power Side-Channel Attack Analysis: A Review of 20 Years of Study for the Layman

Obscure & Undetected: Hacking Into Hardware of Mission-Critical Infrastructure Using Side-Channel Attacks | 2019-11-14 | Security Magazine

PDF) Asynchronous Advanced Encryption Standard Hardware with Random Noise Injection for Improved Side-Channel Attack Resistance
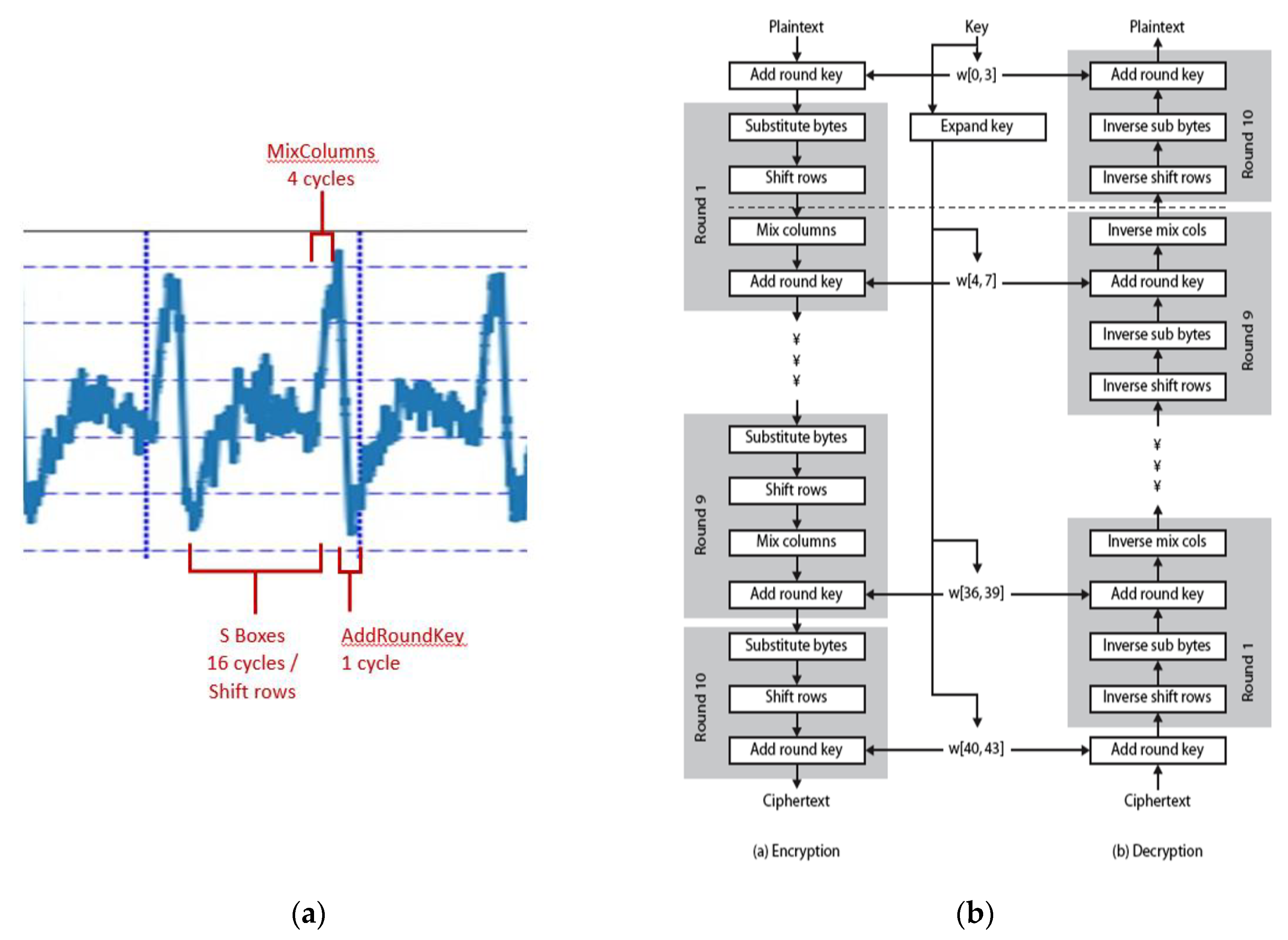
![PDF] AES-Based Security Coprocessor IC in 0.18-$muhbox m$CMOS With Resistance to Differential Power Analysis Side-Channel Attacks | Semantic Scholar PDF] AES-Based Security Coprocessor IC in 0.18-$muhbox m$CMOS With Resistance to Differential Power Analysis Side-Channel Attacks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/dd2547f51a966a0e01805b4f1004e57d258122ab/2-Figure1-1.png)
PDF] AES-Based Security Coprocessor IC in 0.18-$muhbox m$CMOS With Resistance to Differential Power Analysis Side-Channel Attacks | Semantic Scholar
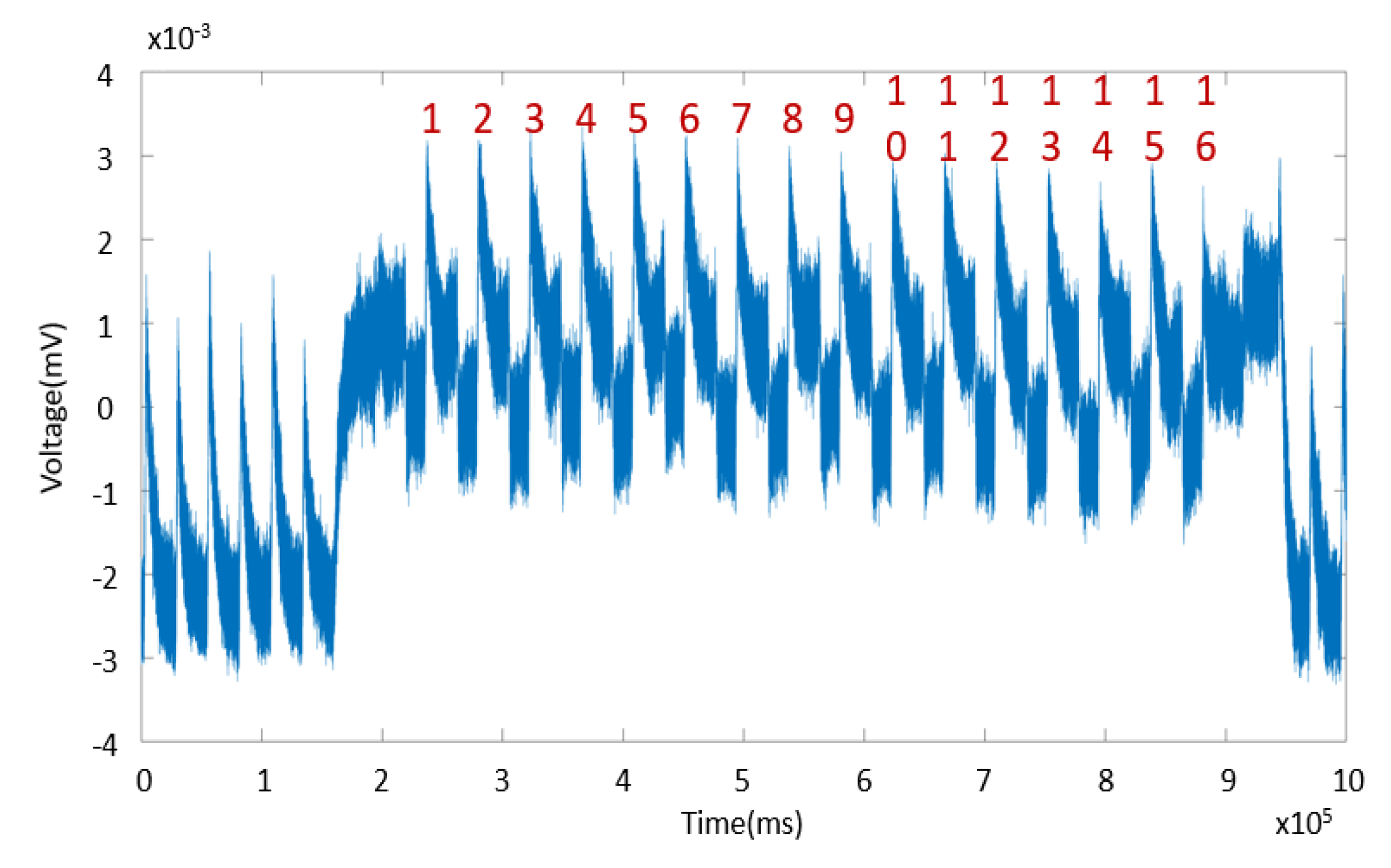
Cryptography | Free Full-Text | Power Side-Channel Attack Analysis: A Review of 20 Years of Study for the Layman

Low‐complexity and differential power analysis (DPA)‐resistant two‐folded power‐aware Rivest–Shamir–Adleman (RSA) security schema implementation for IoT‐connected devices - Kaedi - 2018 - IET Computers & Digital Techniques - Wiley Online Library

Applied Sciences | Free Full-Text | A Low-Overhead Countermeasure against Differential Power Analysis for AES Block Cipher
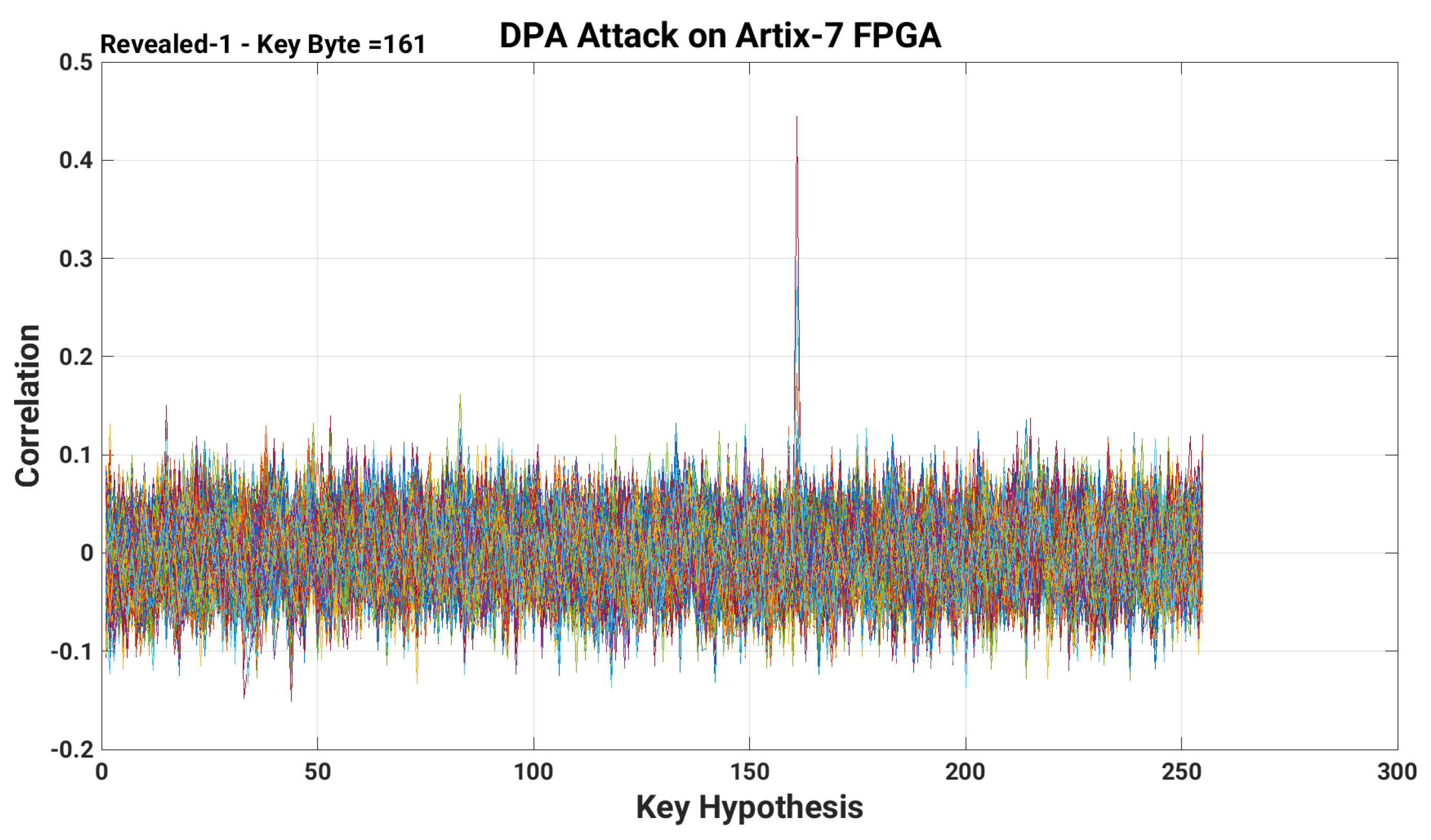
Applied Sciences | Free Full-Text | A Low-Overhead Countermeasure against Differential Power Analysis for AES Block Cipher