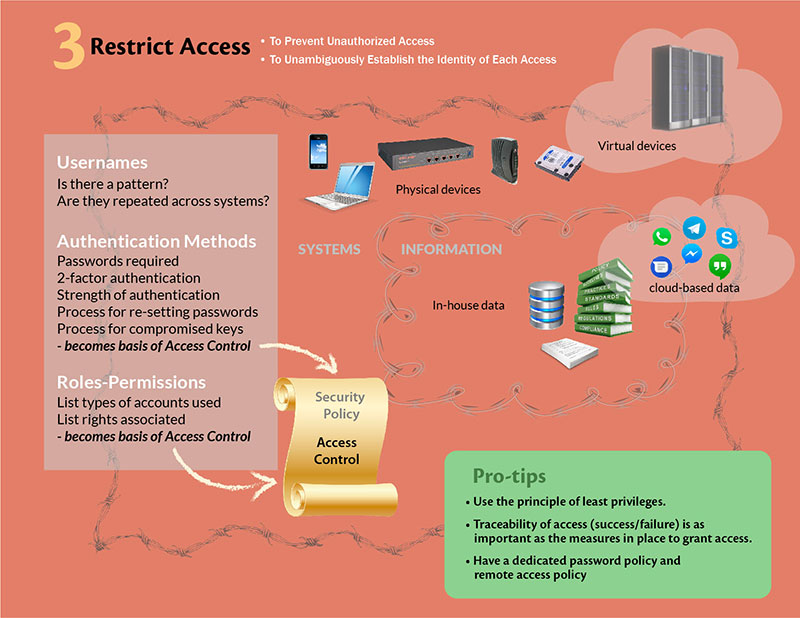
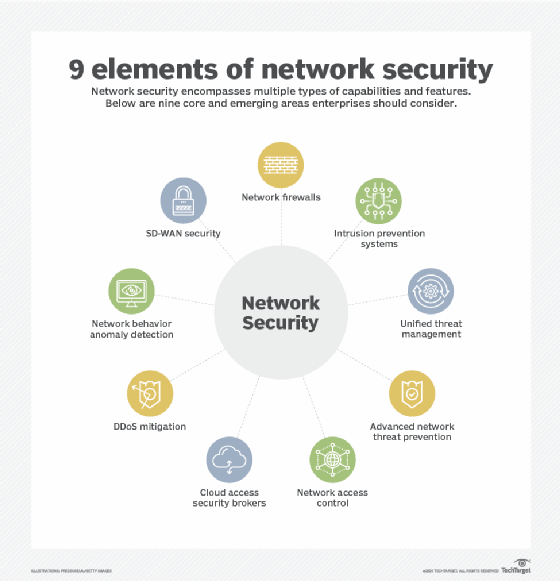
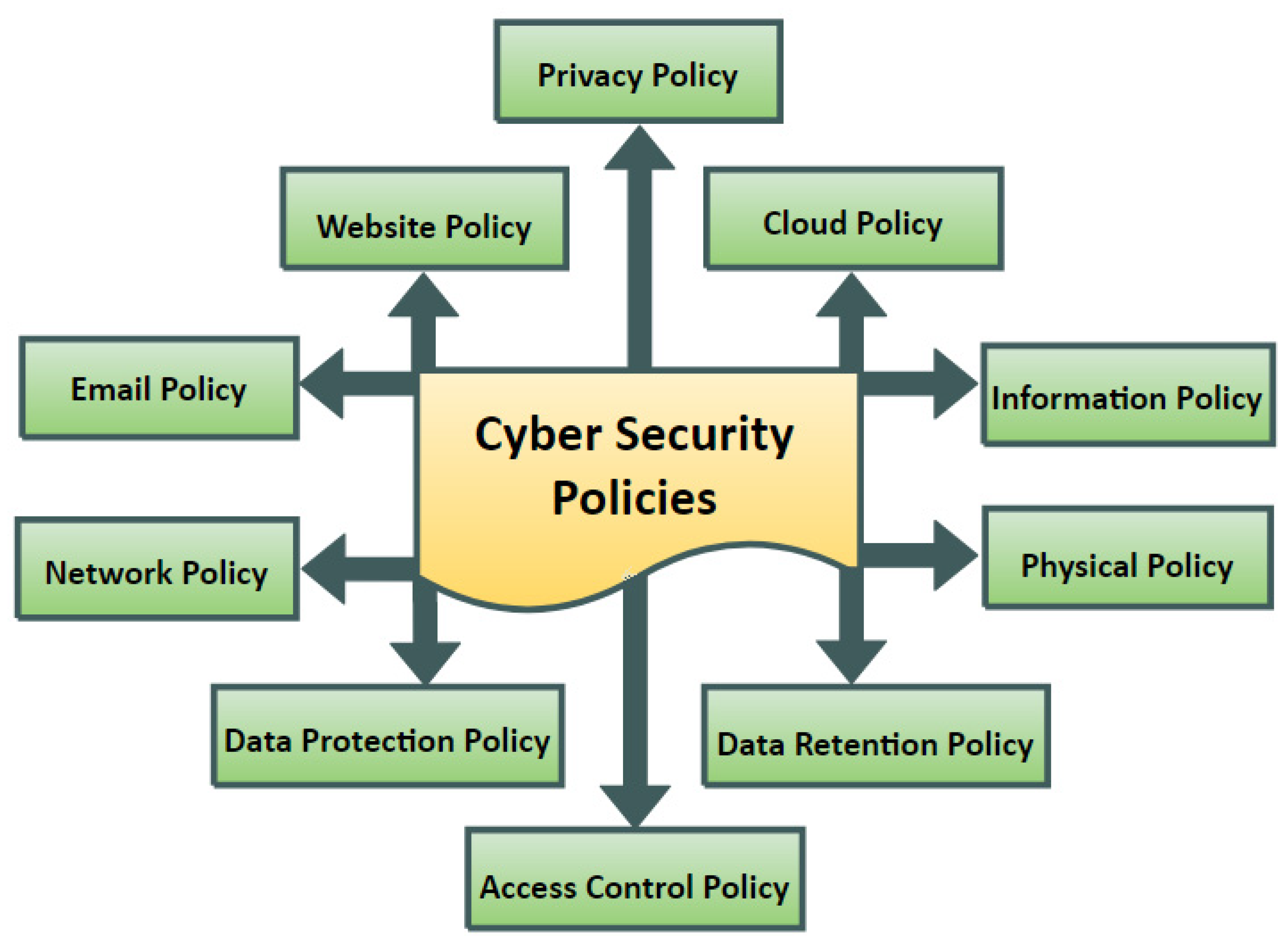
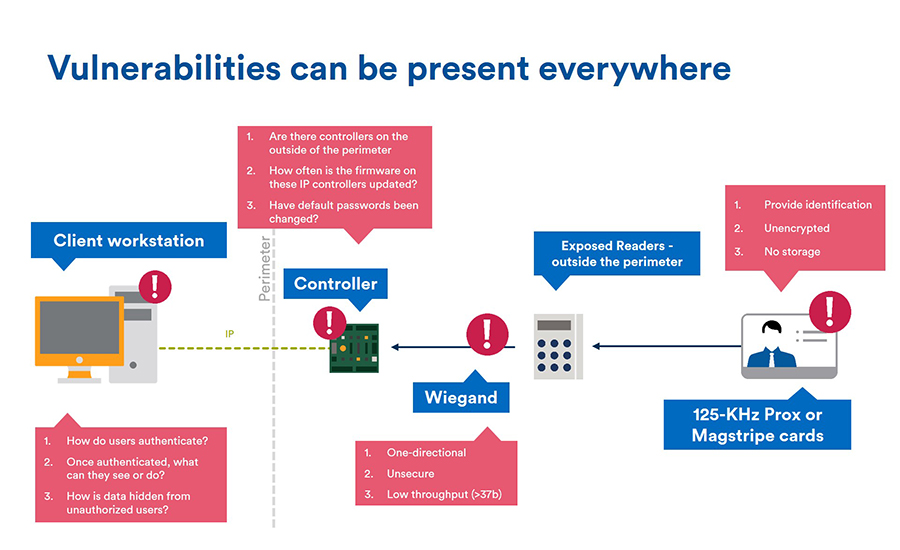
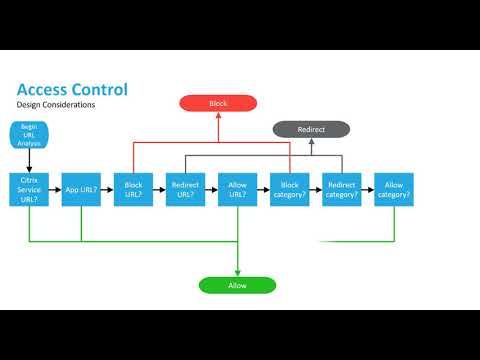
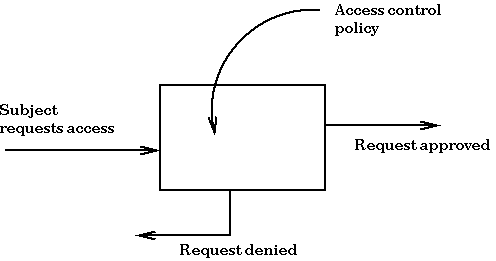
Information Security Define Access Control Measures For Employees Ppt Icon Pictures PDF - PowerPoint Templates

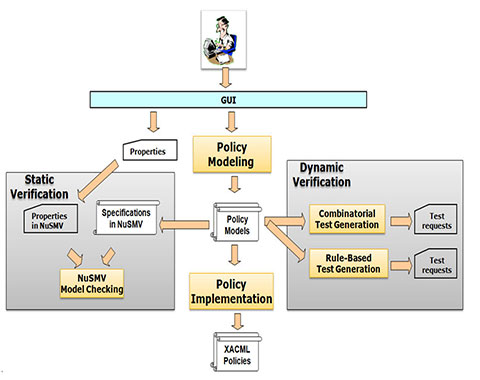
A systematic review on security in Process-Aware Information Systems – Constitution, challenges, and future directions - ScienceDirect