
Searching for VPN IP Exposure Through Criminal IP and Recommendations for Protective Measures | CIP Blog

VMware on Twitter: "At #VMworld 2020, CloudHealth Secure State has announced new capabilities to combat multi-cloud security & compliance risks. Learn more in this blog post 📄: https://t.co/IKS4VWU56c https://t.co/C4Qh4WrrkK" / Twitter

Remote monitoring of autonomous sensors is a serious IoT security risk... | Download Scientific Diagram

![What can someone do with my IP address? [updated] | NordVPN What can someone do with my IP address? [updated] | NordVPN](https://nordvpn.com/wp-content/uploads/blog-social-what-can-someone-do-with-your-ip-address-1200x628-1.png)







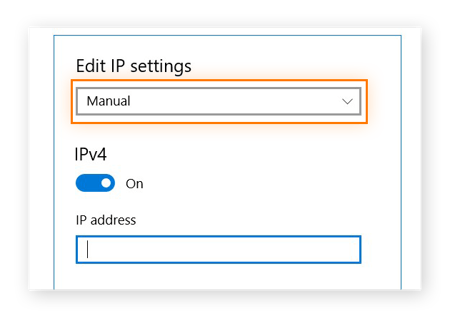




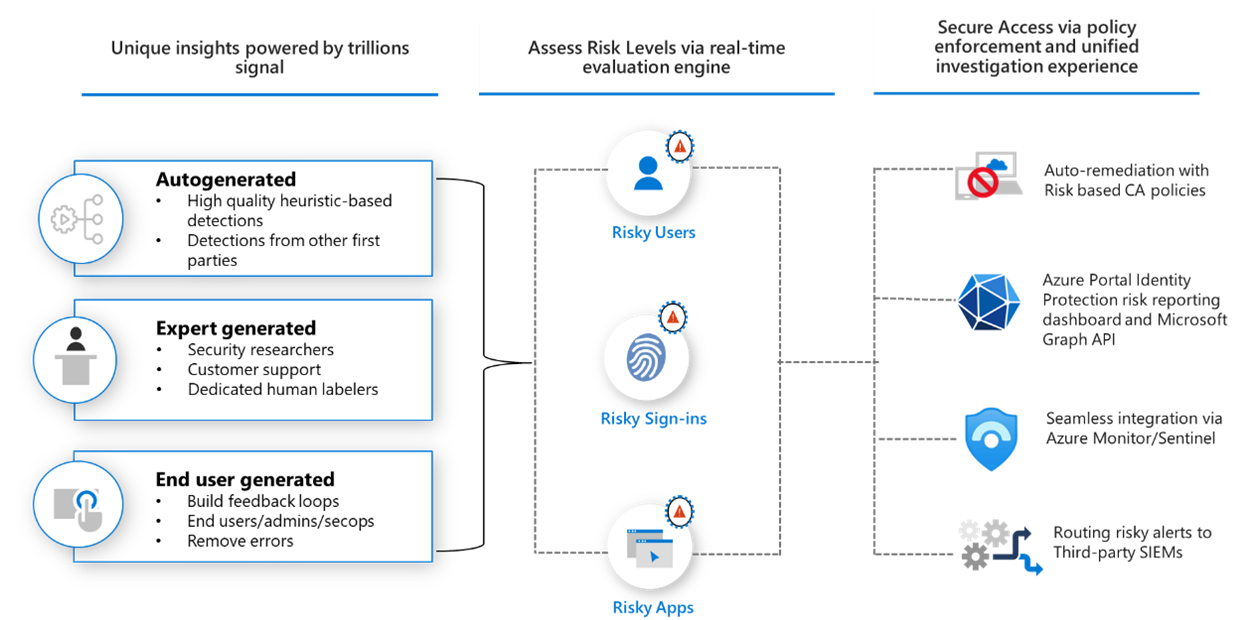
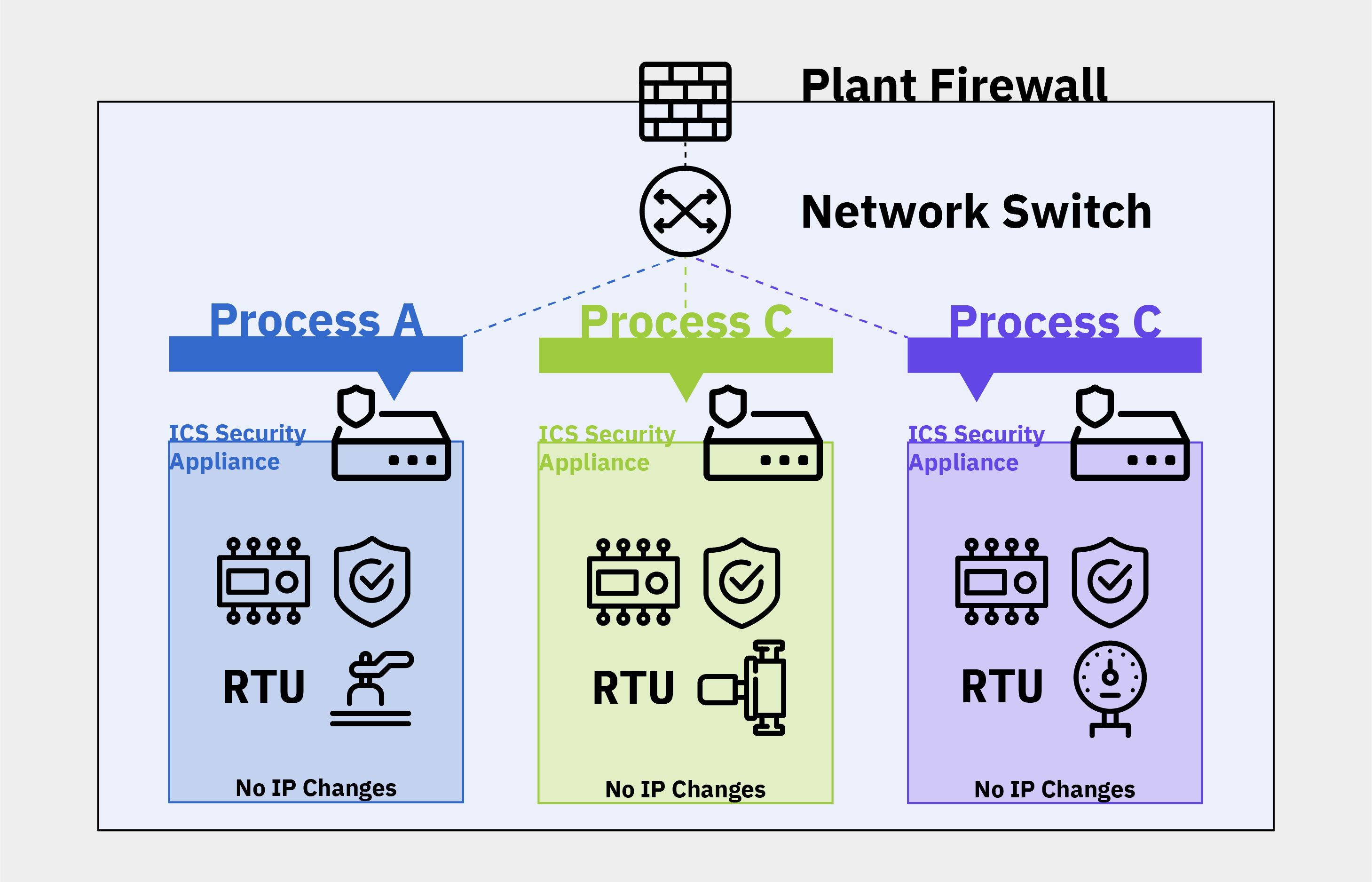

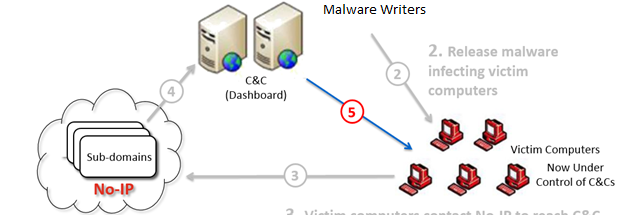

.png)
![Analyst Report] Open Source Security and Analysis Report | Synopsys Analyst Report] Open Source Security and Analysis Report | Synopsys](https://www.synopsys.com/content/dam/synopsys/sig-assets/images/ossra-2023-coverset-optimizedB.png)